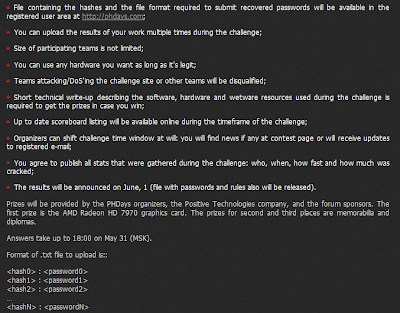
I recently participated to the Hash Runner challenge ran by
http://ptsecurity.com/ during their "Positive Hack Days" or "PHD" forum (held on 30/31 May).
The idea is quite simple, you are given a list of hashes of different types and you have 24 hours to crack as many as possible.
I started the contest arround 5 hours late as a one man team, so only me "Xanadrel" from France. I was also in team hashcat for past "Crack Me If You Can" challenges in 2010 and 2011 (which I joined in the end of the contest as I said them when starting Hash Runner that I was ok to give my plains to them), but this time I wanted to see how good I was alone, that was the point.
The hardware used was :
- my main PC : i7 950, 1x 5770 and 1x 7970
- one i5 2300k core for 4 lm hashes
- a pencil
Software used :
Hashcat, oclHashcat-plus, ophcrack, rcracki_mt, passwordspro, maskprocessor, notepad++ (for copy/pasting hashes), brain ?
Once I was ready for the contest I grabbed the list of hashes and split them by hand (copying hashes of a certain type, removing type note and ":" chars) in files like this :
dcc2.txt
des.txt
lm.txt
md5.txt
md5_pass.salt.txt
and so on...
In the meantime I ran the LM hashes with ophcrack (took arround 5:30 hours to finish).
Then I started to crack the hashes with straight wordlist attacks and some basic/common rules in hashcat and in passwordspro for the GOST hashes.
I also noticed some things were wrong to me, such as DES (couldn't crack a single one during the contest), or phpbb3, ssha, wordpress hashes (their length was uncommon and couldn't crack them with hashcat).
Later, atom made a custom oclHashcat-plus version to support the phpass and DCC2 hashes, which I used.
With the few plains I found I started searching for patterns, noticed things like dates (dd.mm.yyyy) or appending years (yyyy) to words.
The wordlists used were :
- Custom/previously found plains by me
- facebook-firstnames (a lot of plains were based on names)
- common small dicts for slow algorithms + rules
- well known wordlists such as phpbb or rockyou
A few hours after the start I tried other things like rules to prepend/append or both 1/2 chars (well it was mostly special chars) to the words or rules to duplicate words as I saw a few plains like that.
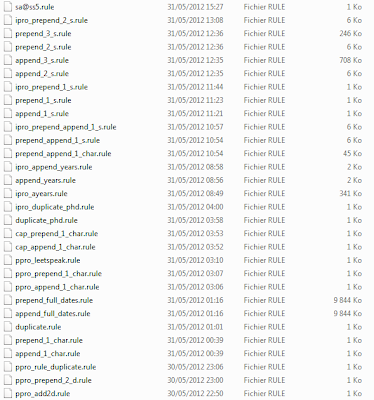 |
| Examples of rules tried |
Noticed some leetspeak plains like : h3rrm@nn or r0ch3573r, so used rules for this and made a smaller rules file based on leetspeak for slow algos.
When ophcrack was done with the LM hashes there were 8 left hashes, found 4 of them running rcracki_mt with the lm_all_space tables.
Near the end I noticed that I didn't really run bruteforce attacks, so I found some passwords like : 6{x#_a or 9Mv)0. There were also passwords in the form : dd<month>yyyy (08march1924 for example), made rules to append/prepend the year/day and a wordlist with only months.
And if you were wondering why I used a pencil here is the answer, to press the "q" key only if I really want to stop a long oclHashcat run.
To submit the hashes I was copy/pasting the found plaintexts and replacing ":" with " : " in notepad++ and put them in a file to upload, later I did "cat *.out > found.out.txt" to have all found hashes in a single file and upload them all at once.
Plaintexts found per type (approx) :
31 DCC2
108 md5
54 md5(pass.salt)
77 mssql2005
114 ntlm
79 phpbb3
106 sha1
96 sha256
91 MySQL5
383 LM
42 wordpress
74 GOST
During the contest I "fought" against InsidePro Team hoping to get the first place but they finally took a great advantage and before the end teardrop took the 2nd and then the 1st place, so congratulations to them, they did a great job.
Thoughts about the contest :
- the "hash : plain" format was annoying, but maybe it was made on purpose :p
- I still can't figure out why no DES was found
- the points system was good ( like 10-300 points, compared to last CMIYC where hashes weighed from 1 to 16000 points)
- it would have been more convenient for the forum/contest to take place during the week-end
As a conclusion I would say that 1st place was maybe too much but with a 3rd place (less than 5k points behind InsidePro) I'm quite proud of what I did and I enjoyed the contest (thanks to PHD staff for organizing such a contest), if there is another one next year I will participate too.























